Ethical Hacker Career Options
What is ethical hacking? Have someone asked you this question and you got confused? What is ethical hacking exactly? If it’s hacking then how it can be ethical?
Also, if you told someone that you want to become an ethical hacker, some people might get thoughts like… Really? Can hacking be ethical? Well, in that case, let me describe to you that….Yes! Hacking can be ethical. Hacking which is done to defend & not to attack is ethical. Furthermore, Ethical hacking is one of the most demanding career options for IT professionals.
Ethical hacking entails an accredited attempt to gain unauthorized access to a computer system, data or application. Carrying out an ethical hack includes duplicating strategies & operations of malicious critics. It is Also known as the “white hats technique of hacking,” ethical hackers are security experts that perform these assessments.
Overview of ethical hacking jobs
The job vision for IT security is presumed to grow by 40% from 2020 to 2030.
The reason for this rise is the expanding frequency of cyber threats & security incidents. To administer these occurrences, we need a strong line of defense that involves Ethical Hackers.
As with other computer and network security roles, ethical hackers are in high demand, and this demand is only increasing as the severity and cost of cyber attacks continue to surge.
Ethical Hacker salary in India
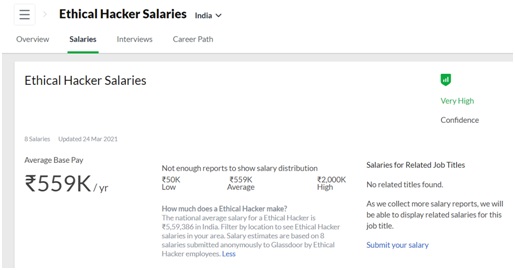
In India, a certified ethical hacker or just certified ethical whom we can say freshers earns an average salary of Rs 3.5 lakh per year which increases with experience cumulatively up to more than 15 lakh per year.
According to glassdoor recent research
The national average salary for an Ethical Hacker is ₹5,59,386 in India. Filter by location to see Ethical Hacker salaries in your area.
According to glassdoor Salary estimates are based on 8 salaries submitted anonymously to Glassdoor by Ethical Hacker employees.
You can apply for Ethical Hacking Jobs on portals like Naukri.com will give you an idea about your job roles and required skills.
Organizations are looking for professionals with specialized knowledge making it convenient for certified ethical hackers to take up other cyber security jobs, too.
These are just a few of the professional profiles that an ethical hacker can easily fit into are below listed
Information Security Analyst:
Information security analysts command computer network systems to stave off potential security breaches. They control systems by updating software & recommending security updates to superintendence. Information security analysts further work one on one with employees to support them to get new programs & hardware.
Security investigator:
A security investigator guards & patrols an area to prevent theft and violence. He answers calls and investigates any disturbances. A security investigator is also recognized following other job authorities, such as a security guard or store detective.
Penetration tester:
A penetration test, colloquially identified as a pen test or ethical hacking, is a sanctioned simulated cyber attack on a computer system, performed to evaluate the security of the system; this is not to be confused with a vulnerability evaluation.
Web security administrator/manager:
Web Security Administrator develop, implement, and maintain firewall technologies that secure an organization’s websites. and Defines network security issues also develop plans and procedures, & ensure that the safety and privacy of their newly developed internet & intranet sites.
Data security specialist:
Strong problem-solving, analytical, & organizational skills can help you get that done. As an information security specialist, you must be technically savvy also need to work with tools such as intrusion detection systems (IDS) to manage networks from suspicious traffic.
Computer/digital forensics investigator:
Computer forensics investigators, named as computer forensics experts, computer forensics examiners, or computer forensics analysts, are charged with uncovering including describing the data contained on, or the state of existence for a digital artifact.
IT security administrator/consultant/manager:
A security administrator is the main person of a cyber security team. They are typically accountable for installing, administering, & troubleshooting an organization’s security resolutions.
Configuring and supporting security tools like firewalls, anti-virus software, & patch management systems.
Network defense technicians:
A Computer Network Technician is also acknowledged as a Network Technician who manages the network system of a company. Technicians monitor the day-to-day controls of an organization’s internet and computer network. They also assist in installing hardware & software for all the systems.
Conclusion:
As with other computer and network security roles, ethical hackers are in high demand, and this demand is only increasing as the severity and cost of cyber attacks continues to surge



